What You Should Do If You Are Hit With CryptoLocker
Or, if there is a bunch of weird stuff going on in a Word document, don’t ignore it
Sometimes I feel like our office is the Ghostbusters’ firehouse and Gozer the Destructor has come! Meaning CryptoLocker ransomware, which can hide from antivirus and spam filtering systems, is back.
CryptoLocker is designed to extort money from computer users by encrypting files until you pay a fee by a deadline, and threatens to delete your files if that deadline passes. CryptoLocker may be found in suspicious email, such as fake UPS tracking notifications.
This is the third go around we have seen of CryptoLocker, and like the Ghostbusters we have gotten pretty good at jumping to action to eliminate the threat. Unfortunately, while CryptoLocker is readily removed, it may be impossible to unencrypt the affected files. The quicker the threat is identified, the easier it is to fix and the fewer files that are impacted.
How you know you have CryptoLocker?
- Because it can be spread via your company’s servers, you don’t necessarily have to be the person who opened the email to be infected.
- There is no real “event” that will give you a head’s up that you have it.
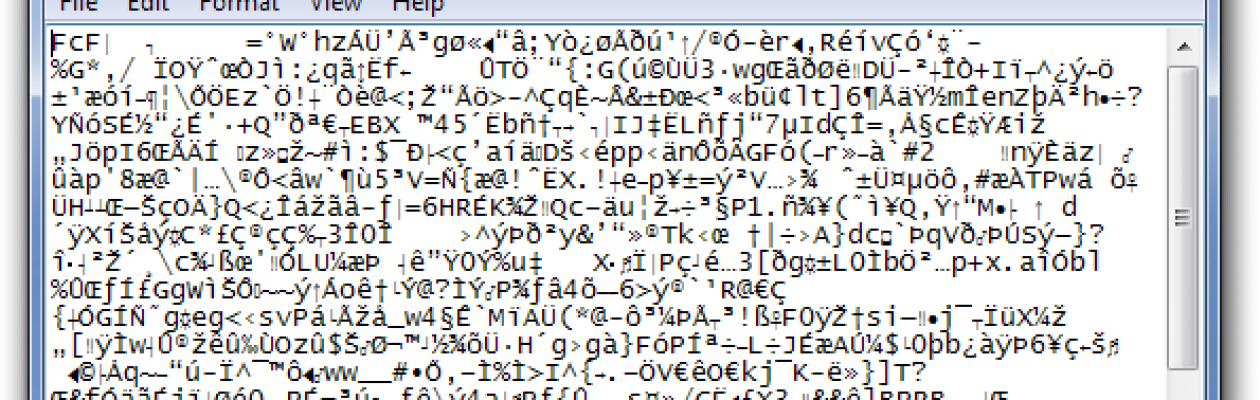
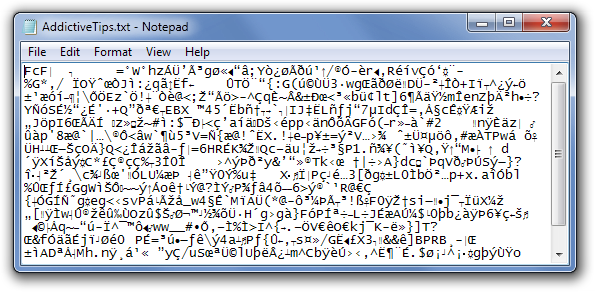
- Your biggest hint will be when you open a Microsoft Word or Excel or an Adobe PDF document it will look like the image below:
What you should do if you think you have CryptoLocker
- Don’t ignore weird looking files like the above.
- Immediately shut down your computer.
- Call us ASAP at 855-559-6637.
Unfortunately, potential solutions for this malware are time sensitive and the sooner the threat is recognized and responded to can potentially save data.
The first response is to try a system restore on the PC however the virus had a built in protocol to delete restore points about halfway through the process. By recognizing the threat we can attempt a system restore before the files are encrypted.
How to protect yourself
As data that is already encrypted is lost, there are several workflow changes that can potentially work to your advantage.
- Store your files in a location that is remote and not attached to your computer. It is preferable to be in a location that is backed up regularly.
- Avoid opening attachments you weren’t expecting or from people you don’t know. If you think it may be a valid e-mail, then call the person to double check if they sent you anything.
- Do not open any attachment that has the file extension .zip or .rar. These will potentially hold a virus.
- If you accidentally click the link and are not sure if it is a virus, then contact the helpdesk immediately. The sooner we counteract the virus the better.